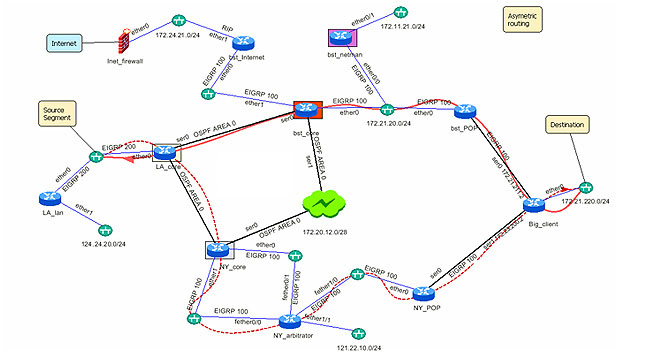
How to Break a Network – about the work of Lieutenant Colonel John Graham studying insurgent (and other networks),was published by David Axe in 2007 – it’s no less relevant now:
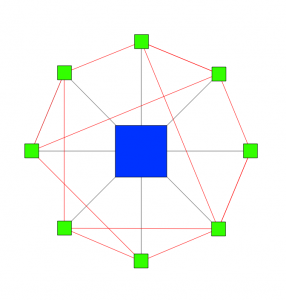
… this morning during presentations at the Association of the U.S. Army show in Fort Lauderdale, Florida, I was jolted out of a depressed stupor when an Army officer slapped a slide up on the projection screen that showed seemingly random points connected by lines: a classic representation of an international terrorist network or insurgent bombmaking cell. “Networks are hard to break,” Lieutenant Colonel John Graham announced. Then he smiled and said he was going to show us how.
Graham is a professor at West Point, where he teaches future officers the very thing he was showing us. The slide, he explained, was in fact a representation of his department: its instructors, students and partners in the Army. ”What I have,” he joked, “is a network at West Point working on networks.”And what have they learned since network studies got serious in the wake of 9/11? That there are three major vulnerabilities in networks:
1) Density nodes: people with many immediate connections, e.g. leaders
2) Centrality nodes: people with fewer immediate connections but who serve as crossroads in many relationships, e.g. financiers
3) Boundary spanners: people with few (maybe just two) connections but who span long gaps between chunks of the network, e.g. liaisons or messengers
Assuming your resources for attacking a network are limited — and in the real world, they always are — who do you hit? Graham asked. Using his own department as an example, he advocated killing just three of the dozens of members. Suprisingly, none were examples of density or centrality, since those were all situated in the meaty middle of the network. The network had enough redundant connections to quickly repair itself after their demise. What Graham wanted to do was hit the network where there were no redundancies, so all of his targets were boundary spanners. By taking out three spanners, Graham showed how you could isolate relatively homogenous chunks of the network, rendering it stupider and less adaptive than before.
Funny thing is, the spanners in Graham’s department’s network were mostly low-ranking members such as cadets. Just goes to show, when attacking networks, the most obvious targets aren’t always the most important.
From David Axe at War is Boring.
Addendum, June 23:
In covering the same conference for Government Computer News, Patience Wait reported in Network science is about more than computer systems
:
Government researchers in fields as diverse as biotechnology, ecosystems and behavioral science are looking for common patterns in the systems they study, to see if they can be applied to the development of robust complex networks, whether for computer systems or organizational structures.
A panel convened at the Association of the United States Army winter symposium yesterday discussed some of the parallels between biological systems, such as the circulatory, respiratory and central nervous systems in fish, the behaviors of proteins in bacteria and the organization of an airline’s flight routes, to show how their behaviors may be mirrored in the performance of networks.
Understanding biological, molecular and economic networks is necessary to design large, complex networks whose behaviors can be predicted in advance, said Jagadeesh Pamulapati, deputy director for laboratory management and assistant Army secretary for acquisition, logistics and technology.
The search centers on finding the answer to, ‘What are the underlying rules in common?’ he said. Can a common language be used to describe all these systems? Is there a mathematical formula to describe their behaviors and relationships?
Jaques Reifman, chief scientist for advanced technology and telemedicine in the Army’s Medical Research and Materiel Command, said that modeling protein interactions inside e. coli and plague bacteria is a form of comparing networks to understand ‘why in two related viruses, sharing more than 50 percent of proteins, one’s more virulent, more deadly, than the other.’
Reifman offered the theory that proteins can be judged for ‘essentiality’ based on how many connections they make with other proteins, and these hub proteins are more likely to be centrally located within the network of interactions.
‘I study fish because it’s the data we can get,’ said Lt. Col. John Graham, assistant professor for behavior sciences and leadership at West Point. Humans are resistant to providing access to their e-mail traffic, for instance, to allow the generation of very large datasets for study. But the understanding of networks is critical, he said, because ‘the bad guys are getting good at network science.’